Hello Friends,
Welcome To Notebility!
What is an Authentication Bypass?
Introduction
Applications require some credentials for example Username, Email, Password, etc. To get access to the system.
In general, authentication bypass is the vulnerable point from where attackers gain access to the system and they gain access to the user’s private information.
they do whatever they want. they may block the users or they use the information in other ways.
Authentication bypass vulnerability is generally caused when it is assumed that users will behave in a certain way and fail to foresee the consequences of users doing the unexpected.
What’s the issue behind the Authentication Bypass?
Authentication bypass exploit is mainly due to a weak authentication mechanism. And it causes real damage to the user’s private information because of weak authentication.
Methods to bypass the authentication schema
There are so many methods to bypass the authentication schema in use by a web application. Here are some of the common ways to bypass authentication
- SQL Injection
- Parameter Modification
- Session ID Prediction
- Direct page request (Forced Browsing)
There are several way to Bypass the Authentication But we are going to talk about the SQL Injection
It was found out that SQL Injection techniques can be used to fool the application into authenticating without the attacker needing valid credentials.
SQL Injection vulnerabilities on login pages expose an application to unauthorized access and quite probably at the administrator level, thereby severely compromising the security of the application.
We have used- ‘=’ ‘or’ code to bypass authentication
Let’s take example for sql injection used to bypass authentication,
There is login form which I want to bypass the authentication
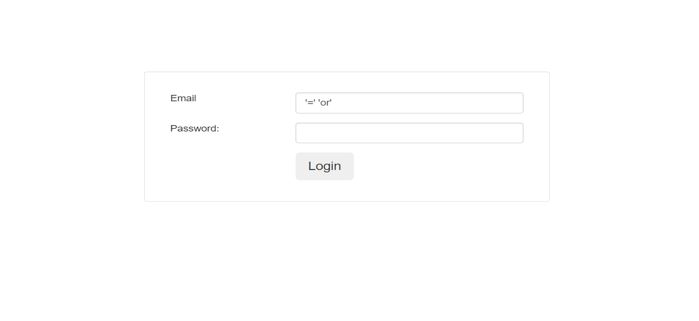
Simply I used only ‘=’ ‘or’ in email input and I could bypass the authentication. And gain the access of users information.
How to stay protected
This vulnerability can be eliminated by fixing the SQL injection vulnerability in the application’s authentication mechanism.
The authentication bypass vulnerability is a special case of SQL injection, specifically located in your authentication routines.
The following recommendations will help to mitigate the risk of Authentication Bypass attacks
- Keep up to date on patches and security fixes as they are released by the vendor or maintainer
- You always check for all vulnerabilities and always install the best antivirus software and are always free from bugs.
- To Avoid the special character ‘=’ ‘or’ to bypass authentication, you can use the “ mysqli_real_escape_string() “.
- It is best to have a secure and strong authentication policy in place.
- Avoid using external SQL interpreters.
- It is best to ensure all systems, folders, apps, are password protected.
- Audit your applications frequently for points where HTML input can access interpreters.
- Security experts recommend resetting default passwords with unique strong passwords and periodically rotate passwords.
- It is suggested to not expose authentication protocol in the client-side web browser script.
- They suggest ensuring that user session IDs and cookies are encrypted.
- It is recommended to validate all user input on the server side.
- Avoid the use of dynamic SQL or PL/SQL and use bound variables whenever possible.
- Enforce strict limitations on the rights to database access.
- Remove any sample applications or demo scripts that allow remote database queries.
Thanks for reading…